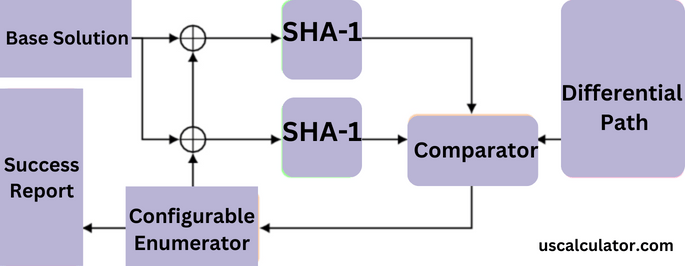
SHA 1 Generator
What is a SHA1 Generator? A SHA1 Generator produces a 40 hexadecimal (160-bit) hash value from any input, commonly used for data integrity checks. or used as a Key to protect important data such as credit cards, private information, and much more.
Share This Generator
Related Calculators
About SHA 1
Once a master of digital fingerprinting (cryptographic hash algorithms), SHA-1 is now regarded as a little outdated. Think of it like the ancient lock on your grandmother’s basement; it worked well once, but not so well these days. The main points are as important: Any digital material (text, files, or communications) may be converted into a unique code, similar to a fingerprint, using SHA-1. This code, known as a hash, is useful for determining whether something went wrong throughout the process. The issue? The coding of SHA-1 was cracked by clever people, rendering it unreliable for critical information. So what ought to be used in its place? Secure, more recent algorithms like SHA-256 are far more difficult to crack, much like the sophisticated fingerprint scanners on your phone. In summary, use a more secure hashing method, like SHA-256, for anything significant; SHA-1 is fine for some older systems or non-critical data. Be cautious when navigating the internet world!
Visit Wikipedia to learn more about the SHA-1 generator.
If you have any confusion or doubt then double-check with our SHA 1 Generator.
On the Cost of ASIC Hardware Crackers: A SHA-1